What is MPC (and Why Should I Care)?
Background
If you’re an app developer building with crypto, you’ve probably heard about MPC, or Multi-Party Computation. MPC is a way to perform secure and private computation, and has been popular for institutional crypto asset management as well as in some end-user wallets for a while. However, more recently, with the rise of embedded wallet infrastructure, it has now become possible for application developers to directly integrate MPC into their products.
While MPC makes it easier for more people to safely own and use crypto, making a choice about how to integrate MPC into your application is complex and nuanced. To evaluate and choose the right way to add MPC to your product, you’ll need to:
- Understand the technical nuances of different MPC offerings - these can significantly influence your app security and user experience.
- Ask detailed questions about the specifics of the infrastructure you’re going with.
- Evaluate highly technical products that are described in ways that are sometimes confusing - or even misleading.
This article is meant as a guide to help you evaluate offerings through the lens of security, usability, and relevance to your users.
Note: If you don’t need any background on Threshold Cryptography, Shamir Secret Sharing, or MPC and just want a guide on evaluating solutions, skip to this section
Threshold Cryptography
Threshold cryptography is a field of cryptography broadly focused on securing or concealing information by distributing it across a number of parties n, and requiring some threshold t of those parties to collaborate to reveal the information.
In the crypto space, techniques in this field are used in a number of applications ranging from consensus to zero-knowledge. In this article, we will be focused specifically on applications of threshold cryptography for key management, namely distributing shares of a private key and requiring a quorum of parties to collaborate to sign with this key.
Note: We’ll be using the notation t of n in this article. Broadly speaking, this notation refers to threshold cryptographic schemes where n shares are created to protect a secret (in this case a private key), and some threshold t of shares are required to access this secret (in this case, to provide a signature from the private key). We also recommend this blog post for a deeper dive on techniques using threshold cryptography.
Shamir Secret Sharing and Multi-Party Computation are two prevalent mechanisms for distributing responsibility for private keys. It is important to understand the distinctions between them, as they can impact your application. Below are visuals illustrating the difference between both mechanisms. For simplicity, the images show a 2 of 2 scheme, but the diagrams apply to any threshold and number of shares.
Shamir Secret Sharing

Shamir Secret Sharing is a technique where private keys are split into n shards. These shards can be shared among friends or put in different locations. When a user wants to sign a transaction, these shares need to be combined to reconstruct the signing private key. Shamir Secret Sharing has been widely used in many embedded wallet products today. Typically, shares are recombined in the browser to form the full private key in order to sign transactions.
Often times, Shamir Secret Sharing will be referred to as MPC in marketing or other general communications. When you’re speaking with different infrastructure providers, DYOR and ask about how keys are created, stored, and used for signing to understand what you’re using.
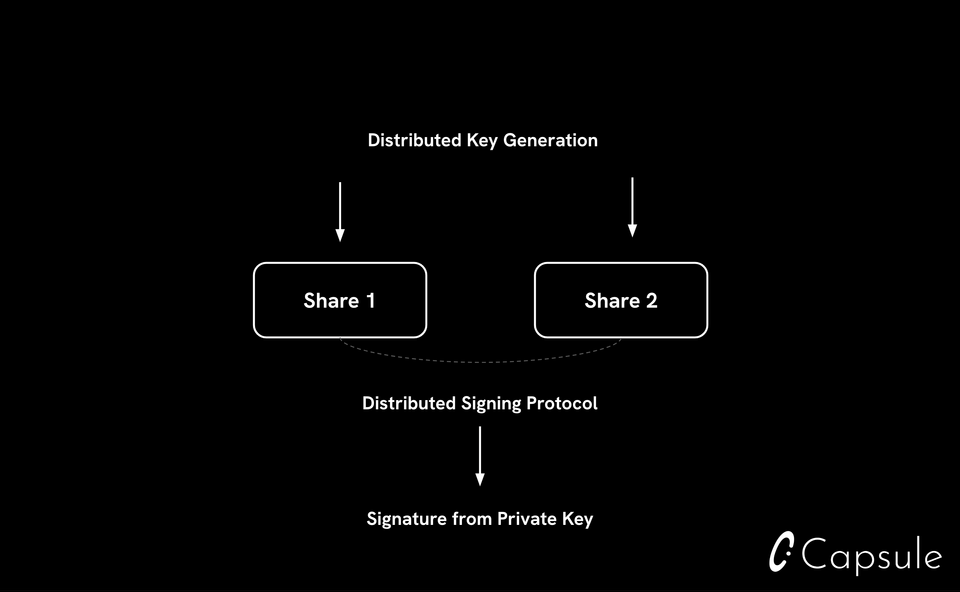
Distributed MPC
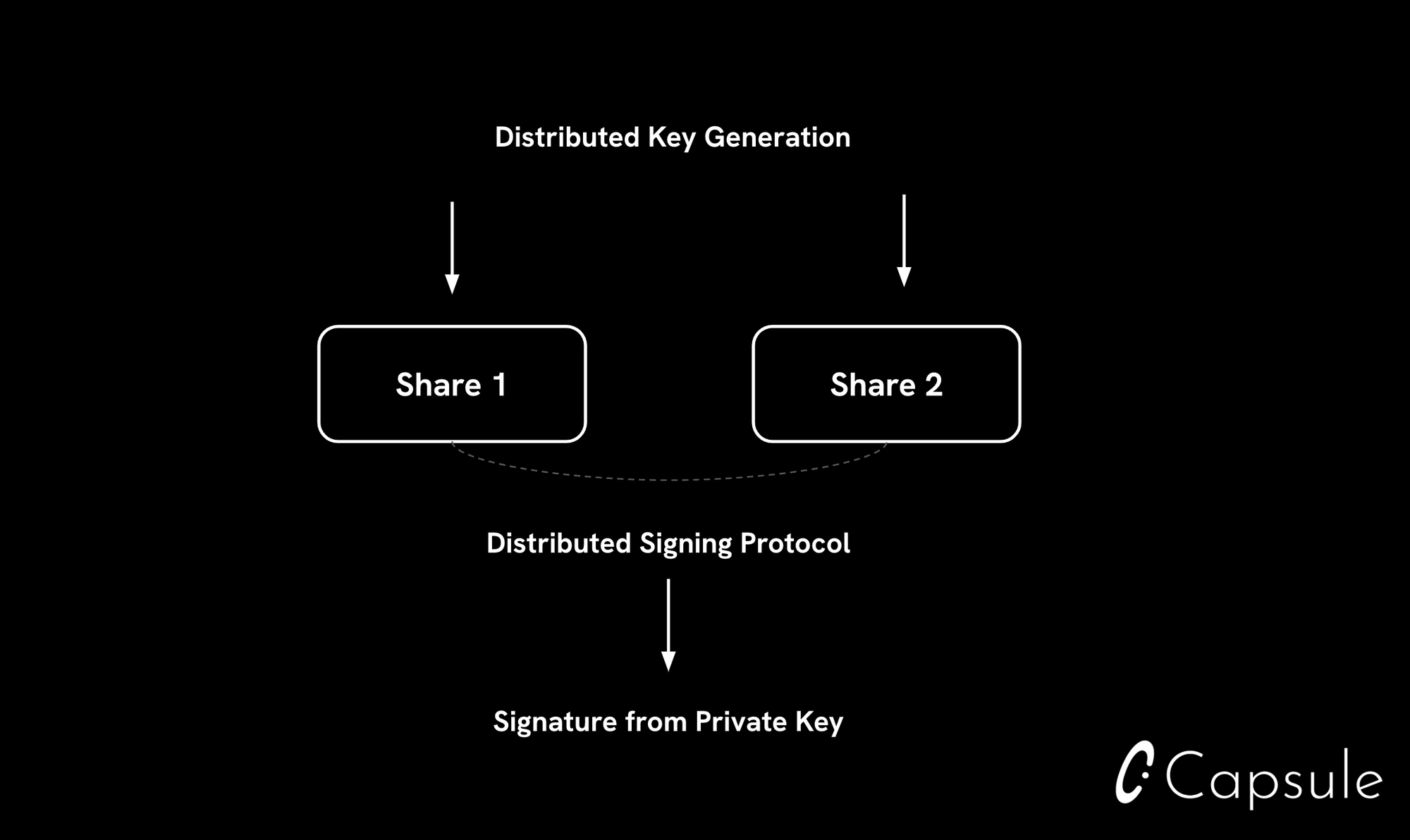
MPC has applications across diverse fields ranging from biology to advertising. In web3, it’s used for managing crypto assets.
MPC empowers multiple parties to perform secure computation while keeping the details of their computation private. MPC ensures no party has to compromise sensitive information during this process, and that no party ever needs to view the full secret. Distributed MPC has two important properties:
- Distributed Key Generation (DKG)
- Distributed Signing
A DKG ceremony consists of the n shares required to sign being generated in disparate (or distributed) locations. Distributed signing enables a signature from the underlying secret to be generated in a distributed manner (vs needing to recombine the key into one place). Two advanced cryptographic techniques, Zero Knowledge Proofs (ZK-Proofs) and Fully Homomorphic Encryption (FHE), keep details of computation secure and provide privacy between participants.
Why this matters
In the context of embedded wallets, this means that keys are never reassembled or reconstructed in one place. Additionally, this scheme removes the need for a third party application or infrastructure to have access to a private key at any point — however this may not necessarily be the case as MPC schemes and the resulting guarantees can vary by provider. When evaluating solutions, ask how keys are generated and how transaction signing works at a technical level.
Note: Capsule uses distributed MPC. To learn more, check out our docs.
Evaluating MPC Schemes
If you have decided you’d like to use MPC, here are a few tips for evaluating solutions. Note: this post does not go into the details of comparing different algorithms within the umbrella of MPC- if you're curious about this, please get in touch!
MPC designs consist of several different t of n schemes, such as 2 of 2, 2 of 3, or 3 of 5. Instead of going purely off of the number of parties and threshold or algorithm used to determine security, you may want to ask some of the following questions:
- Can your provider enable the same wallet exist on and be accessed from multiple devices (eg. a laptop & a mobile device)?
- Does your provider support multiple forms of authentication like email auth or social login?
- How performant is the system and how does that change under load? What do benchmarks look like for wallet generation and transaction signing?
- Is the scheme censorship resistant? How is this achieved?
- What is the end user experience? (eg. How are shares presented to users? Can a user recover access to their wallet? How are transactions signed?)
- What use cases are typically supported by this provider?
What about solutions that don’t do MPC or threshold cryptography at all?
There are several solutions that do not use MPC at all. They may be leveraging passkeys, session keys, or another mechanism to gate access to private keys managing EOA (externally owned account) wallets and an authentication solution as a way to manage user accounts and access.
Depending on your needs, solutions of this type may cause restrictions for your application, especially with multi-device support, email authentication, etc.
Summary
In the end, the choice of which technology to use is up to you and the needs of your product. For further reading on how to leverage MPC with technologies like account abstraction, check out this post.
To learn more about how Capsule uses MPC, get in touch via Twitter or email us at hello@usecapsule.com. If you're a developer who would like to get started with Capsule, check out our docs and join our beta

